Building an Effective Incident Response Playbook: Essential Steps for Cybersecurity Teams
Building an Effective Incident Response Playbook: Essential Steps for Cybersecurity Teams
When a security incident strikes, every second counts. The difference between a minor disruption and a catastrophic breach often comes down to how quickly and effectively your team responds. A well-crafted incident response playbook serves as your team’s GPS during the chaos of a cybersecurity crisis.
What is an Incident Response Playbook?
An incident response playbook is a comprehensive guide that outlines the specific steps, procedures, and responsibilities for handling different types of security incidents. It transforms theoretical incident response frameworks into actionable, step-by-step instructions that can be executed under pressure.
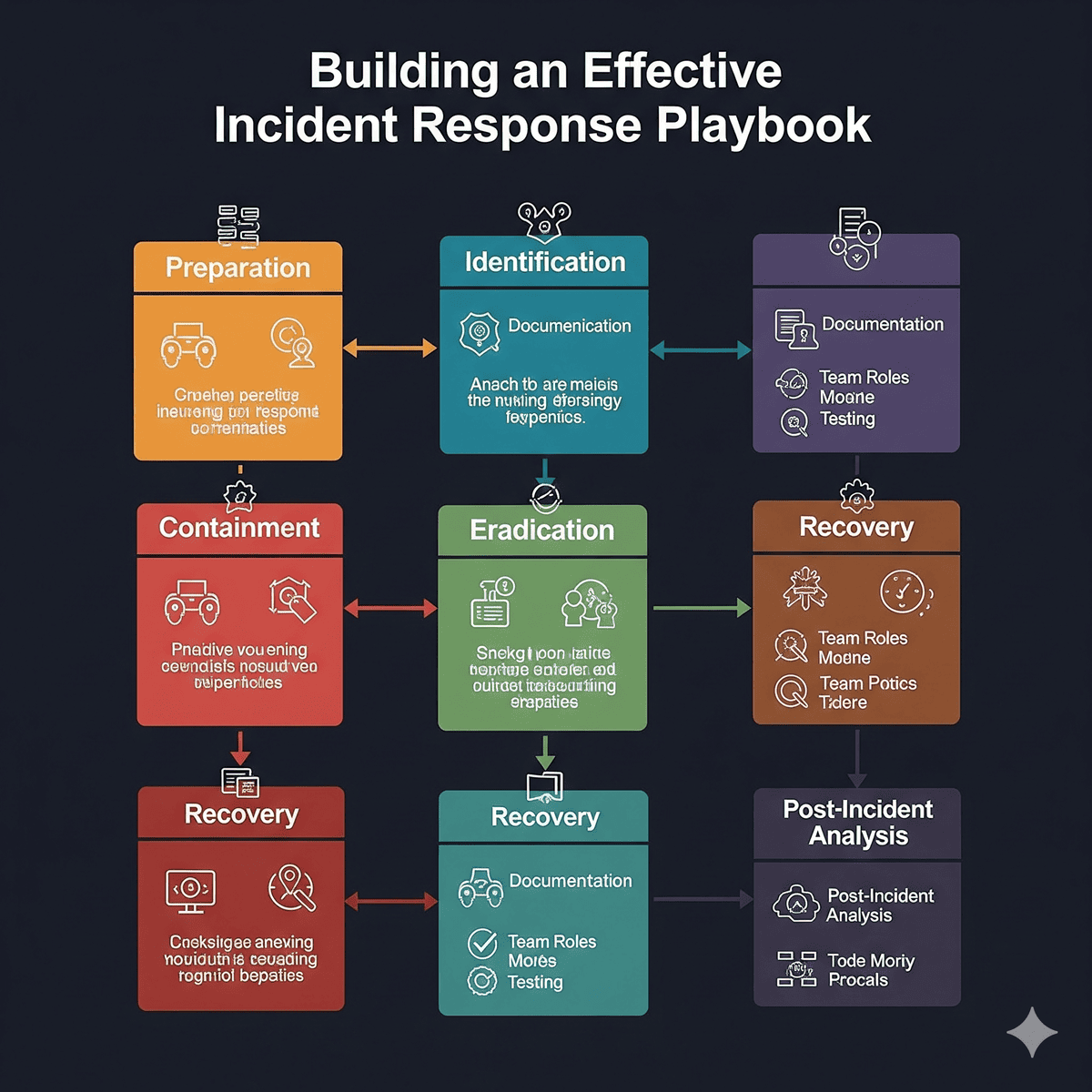
The Six Phases of Incident Response
1. Preparation
Objective: Establish and maintain an incident response capability
Key Activities:
- Develop incident response policies and procedures
- Assemble and train the incident response team
- Acquire and configure incident response tools
- Create communication templates and contact lists
Critical Success Factors:
- Executive sponsorship and support
- Regular training and simulation exercises
- Up-to-date asset inventory and network diagrams
- Pre-configured forensics and analysis tools
2. Identification
Objective: Determine whether an incident has occurred
Key Activities:
- Monitor security events and alerts
- Analyze potential indicators of compromise (IoCs)
- Determine incident scope and severity
- Document initial findings
Detection Sources:
- Security Information and Event Management (SIEM) systems
- Intrusion Detection Systems (IDS)
- Endpoint Detection and Response (EDR) tools
- User reports and help desk tickets
- Threat intelligence feeds
3. Containment
Objective: Limit the extent and impact of the incident
Containment Strategies:
- Short-term containment: Immediate actions to stop the attack
- Long-term containment: Temporary fixes to restore systems to operational state
- Evidence preservation: Maintain forensic integrity while containing the threat
Common Containment Actions:
- Isolate affected systems from the network
- Disable compromised user accounts
- Block malicious IP addresses and domains
- Apply emergency patches or configuration changes
4. Eradication
Objective: Remove the threat from the environment
Key Activities:
- Identify and eliminate the root cause
- Remove malware and artifacts
- Close vulnerabilities that enabled the incident
- Strengthen security controls
Eradication Techniques:
- Malware removal and system cleaning
- Password resets and credential rotation
- Patch management and vulnerability remediation
- Security control enhancement
5. Recovery
Objective: Restore and validate system functionality
Recovery Process:
- Restore systems from clean backups
- Gradually return systems to production
- Monitor for signs of compromise
- Validate system integrity and performance
Monitoring Activities:
- Enhanced logging and monitoring
- Vulnerability scanning
- Penetration testing
- User activity monitoring
6. Lessons Learned
Objective: Improve incident response capabilities
Post-Incident Activities:
- Conduct post-incident review meetings
- Document lessons learned and recommendations
- Update incident response procedures
- Provide additional training if needed
Creating Incident-Specific Playbooks
Malware Incident Playbook
Immediate Response (0-15 minutes):
- Isolate affected systems from the network
- Preserve system state for forensic analysis
- Notify incident response team and management
- Begin impact assessment
Investigation Phase (15-60 minutes):
- Analyze malware characteristics and behavior
- Identify affected systems and data
- Determine attack vector and timeline
- Assess potential data exfiltration
Containment and Eradication (1-4 hours):
- Remove malware from infected systems
- Apply security patches and updates
- Reset compromised credentials
- Update security controls and signatures
Data Breach Playbook
Critical First Steps (0-30 minutes):
- Assess the scope and nature of data compromised
- Activate legal and compliance teams
- Preserve evidence and document timeline
- Begin regulatory notification process
Stakeholder Communication (30-120 minutes):
- Notify senior management and board
- Engage external legal counsel
- Prepare customer communication materials
- Coordinate with public relations team
Phishing Attack Playbook
Rapid Response (0-10 minutes):
- Identify and quarantine malicious emails
- Disable affected user accounts
- Block sender domains and IP addresses
- Assess credential compromise
User Protection (10-30 minutes):
- Force password resets for affected users
- Enhance monitoring for compromised accounts
- Send security awareness notifications
- Update email security filters
Building Your Team Structure
Incident Response Team Roles
Incident Commander:
- Overall incident management and coordination
- Decision-making authority
- Stakeholder communication
Technical Lead:
- Technical analysis and investigation
- Tool deployment and configuration
- Evidence collection and preservation
Communications Lead:
- Internal and external communications
- Media relations and public statements
- Regulatory notification coordination
Legal Counsel:
- Legal and regulatory guidance
- Privilege protection
- Contract and liability review
Technology Stack for Incident Response
Essential Tools
- SIEM Platform: Centralized log management and correlation
- EDR Solution: Endpoint detection and response capabilities
- Forensics Tools: Digital evidence collection and analysis
- Threat Intelligence: IOC feeds and threat context
- Communication Platform: Secure team collaboration
Automation and Orchestration
- SOAR Platform: Security orchestration and automated response
- Playbook Automation: Standardized response workflows
- Integration APIs: Tool integration and data sharing
- Reporting Dashboards: Real-time incident status and metrics
Measuring Incident Response Effectiveness
Key Performance Indicators
Speed Metrics:
- Mean Time to Detection (MTTD)
- Mean Time to Containment (MTTC)
- Mean Time to Recovery (MTTR)
Quality Metrics:
- Incident classification accuracy
- False positive rates
- Stakeholder satisfaction scores
Preparedness Metrics:
- Training completion rates
- Exercise participation
- Playbook currency and accuracy
Common Pitfalls and How to Avoid Them
Pitfall 1: Inadequate Preparation
Solution: Regular training, exercises, and playbook updates
Pitfall 2: Poor Communication
Solution: Clear communication protocols and stakeholder mapping
Pitfall 3: Evidence Contamination
Solution: Forensic best practices and evidence handling procedures
Pitfall 4: Premature All-Clear
Solution: Thorough validation and extended monitoring periods
The Role of Managed SOC in Incident Response
A Managed SOC can significantly enhance your incident response capabilities by providing:
- 24/7 Monitoring: Continuous threat detection and alert triage
- Expert Analysis: Experienced analysts for rapid incident assessment
- Response Orchestration: Coordinated response across multiple systems
- Forensic Capabilities: Advanced investigation and evidence collection
- Compliance Support: Regulatory guidance and documentation
Best Practices for Playbook Development
- Keep It Simple: Clear, concise instructions that can be followed under stress
- Regular Updates: Quarterly reviews and updates based on new threats
- Practice Regularly: Tabletop exercises and simulated incidents
- Document Everything: Detailed logging and evidence preservation
- Learn Continuously: Post-incident reviews and improvement cycles
- Automate When Possible: Reduce human error and response time
- Test Your Backups: Ensure recovery capabilities are functional
Conclusion
An effective incident response playbook is your organization’s first line of defense against cyber threats. It transforms chaos into coordinated action and significantly reduces the impact of security incidents. Remember, the best playbook is one that’s tested, updated, and familiar to your entire response team.
The key to successful incident response lies not just in having great tools and procedures, but in building a culture of preparedness and continuous improvement. Start building your playbook today – because when an incident occurs, it’s too late to begin planning.
Ready to enhance your incident response capabilities? Our Managed SOC team has experience handling thousands of security incidents. Contact us to learn how we can help strengthen your security operations and incident response readiness.